A major corporate cyber-attack, costing millions, has again highlighted the escalating threat of cyber incidents, the increasing sophistication of tactics utilised in these schemes, and the need for stronger cybersecurity measures.
An international company’s branch in Hong Kong recently fell victim to a sophisticated scam, losing a staggering HK$200 million (R483m) in a case involving AI-generated “colleagues” in fake video calls. Earlier this month, the South China Morning Post reported how scammers orchestrated multi-person video conferences featuring fabricated participants, including a digitally recreated version of the company’s chief financial officer instructing money transfers.
Acting senior superintendent Baron Chan Shun-ching of the Cyber Security and Technology and Crime Bureau in Hong Kong told the South China Morning Post that the scammers deployed AI to mimic the voices of targeted individuals, adding credibility to their deception.
Despite initial suspicion from an employee, who received a message from what appeared to be the UK-based CFO, the presence of familiar faces in the video call led to 15 substantial transfers to Hong Kong bank accounts.
While investigators have yet to identify the affected company and individuals involved, they noted that publicly available video footage was exploited to create convincing replicas of company officials. No arrests have been made in connection with the investigation.
According to the 13th Allianz Risk Barometer, deepfake video technology designed and sold for phishing frauds can now be found online, for prices as low as $20 (R377) a minute, with voice simulation software already a powerful addition to the cyber criminal’s arsenal.
Deepfake refers to a form of synthetic media generated using artificial intelligence techniques, typically involving the manipulation of audio or video content to depict individuals saying or doing things they never said or did.
Released last month, the annual corporate risk survey identifies the key challenges facing businesses, including digitalisation, climate change, and geopolitical uncertainties. This year, cyber incidents such as ransomware attacks, data breaches, and IT disruptions, rank as the top global risk in the Allianz Risk Barometer – and by a clear margin for the first time.
Read: Critical infrastructure blackouts are SA corporates’ biggest worry
Focusing on the main trends set to drive cyber activity in 2024, the report said threat actors were already using AI-powered language models such as ChatGPT to write code.
“Generative AI can help less proficient threat actors create new strains and variations of existing ransomware, potentially increasing the number of attacks they can execute. An increased utilisation of AI by malicious actors in the future is to be expected, necessitating even stronger cyber security measures,” the report said.
Cyber incidents named top global risk
According to the report, following two years of high but stable loss activity, 2023 saw a “worrying” resurgence in ransomware and extortion losses.
“Hackers are increasingly targeting IT and physical supply chains, launching mass cyber-attacks, and finding new ways to extort money from businesses, large and small,” the report read.
As to which cyber exposures concerned survey respondents most, 59% said data breach, followed by cyber-attacks on critical infrastructure and physical assets and the increase in ransomware attacks. In the context of turbulent geopolitics and the deepening reliance on digital devices, the potential shutdown of critical infrastructure is likely to become a much more concerning risk for businesses in future, respondents believed.
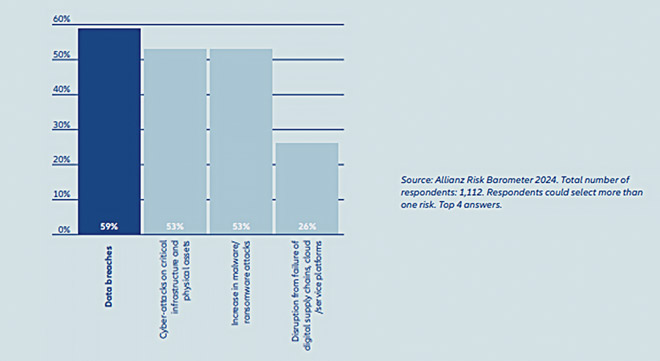
“It is the cause of business interruption that companies fear most, while cyber security resilience ranks as firms’ most concerning environmental, social, and governance (ESG) challenge. It is also the top company concern across a wide range of industries, including consumer goods, financial services, healthcare, and telecommunications, to name just a few,” the report read.
Ransomware on the rise
Ransomware activity alone is forecasted to cost victims $265 billion annually by the beginning of the next decade.
The report said Ransomware-as-a-Service kits, starting from as low as $40, were fuelling this surge, as gangs executed attacks faster, now averaging just four days compared to 60 days in 2019. Claims activity, the report said, was up by more than 50% year-on-year.
Allianz Commercial’s analysis revealed a doubling in cases where data is exfiltrated, from 40% in 2019 to nearly 80% in 2022, with 2023 tracking even higher.
Rishi Baviskar, the global head of Cyber Risk Consulting at Allianz Commercial, said protecting an organisation against intrusion was a cat and mouse game, “in which the cybercriminals have the advantage”.
“Threat actors are now exploring ways to use artificial intelligence to automate and accelerate attacks, creating more effective malware and phishing. Combined with the explosion in connected mobile devices and 5G-enabled Internet of Things, the avenues for cyber-attacks look only likely to increase in the future,” said Baviskar.
Treat your mobile device security with care
According to the report, the pandemic-induced shift to remote work led to the mixing of personal and corporate data on smartphones, tablets, and laptops – often without multi-factor authentication.
Allianz Commercial reported a surge in incidents stemming from inadequate cybersecurity practices surrounding mobile devices.
“Criminals are targeting mobile devices with specific malware to gain remote access or deploy ransomware,” said Baviskar.
“Personal devices often lack stringent security measures and are vulnerable, especially when using public Wi-Fi, increasing exposure to phishing attacks via social media.”
The rollout of 5G technology amplifies concerns, particularly as many IoT devices lack robust cybersecurity measures and are easily discoverable. Combined with the addition of AI, this presents a significant cyber threat, the report said.
SMEs: a growing target
As larger companies bolster their cybersecurity defences, criminals shift their focus to smaller firms.
The report said the cyber risk threat had intensified for smaller and mid-size companies (SMEs), “because of their growing reliance on outsourcing for services, including managed IT and cyber security providers, given these firms lack the financial resources and in-house expertise of larger organisations”.
Allianz cautions that SMEs are particularly vulnerable to the fallout of cyber-attacks, with many lacking the resilience to endure business interruptions. A significant incident, especially for a small company with lax controls or insufficient risk management, could potentially jeopardize its survival.
“SMEs should remain vigilant and have a clear understanding of the risks involved and allocate ample resources in terms of personnel, IT infrastructure, and budget to implement the required security measures,” said Baviskar.
“Initiating a conversation with an MSSP (Managed Security Service Provider) can serve as an excellent initial move, allowing for the creation of an IT budget and strategy tailored to the business’s specific priorities.”
Joint standard on IT governance and risk management
The FSCA and the Prudential Authority (PA) published Joint Standard 1 of 2023: Information Technology Governance and Risk Management in November last year.
The Joint Standard applies to banks, insurers, market infrastructures, managers of collective investment schemes, discretionary FSPs, and administrative FSPs.
Read: Joint standard on how financial institutions should manage their it risks
The Statement of Need states that financial institutions are expected to implement IT controls that are commensurate with their risk appetite, based on the nature and size of the financial institution’s operations.
The Joint Standard becomes effective 12 months after the commencement date of 15 November 2023. This means financial institutions have until 15 November this year to demonstrate compliance with the Joint Standard.



